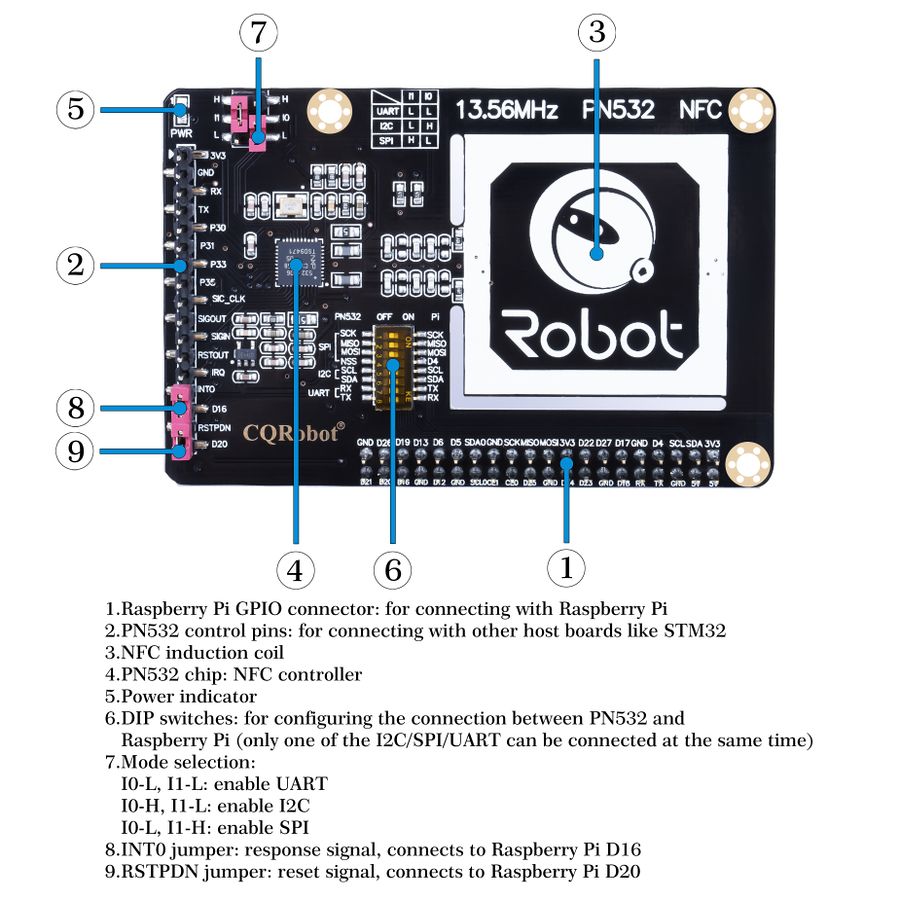
13.56MHz PN532 NFC
Contents
Introduction
PN532 is a highly integrated non-contact read-write chip, which contains the 80C51 microcontroller core (this 8051 user cannot program it, it is a low-level communication protocol stack for built-in NFC), which integrates each of the 13.56MHz an active / passive contactless communication method and protocol.
The PN532 transmission module supports 6 different working modes:
- Reader mode, support ISO / IEC 14443A / MIFARE Mechanism
- Reader mode, supports FeliCa mechanism
- Reader mode, support ISO / IEC 14443B mechanism
- Card operation mode, support ISO 14443A / MIFARE Mechanism
- Card operation mode, FeliCa mechanism
- ISO / IEC18092, ECM340 point-to-point
This is a NFC motherboard based on PN532 operating in the 13.56MHz frequency range. It supports three communication interfaces: I2C, SPI, and UART.
NFC (Near Field Communication) is a wireless technology allows contactless point-to-point data communication between devices within a short distance of 10 cm. It is widely used in applications such as access control system, smart tickets, meal card, etc.
Based on the popular NFC controller PN532 with multi interface options, this motherboard will easily enable NFC function for your Raspberry Python/C, STM32, Arduino.
Features
- Standard Raspberry Pi 40PIN GPIO extension header, supports Raspberry Pi series boards.
- Onboard PN532 chip, supports various NFC/RFID cards like MIFARE/NTAG2xx, etc.
- Three interface options: I2C, SPI, and UART, configured via jumpers and switches.
- Breakout control pins, for easily connecting with host boards like STM32/Arduino.
- Comes with development resources and manual (examples for Raspberry Python/C, STM32, Arduino)
Note
- This module can only be used to write/read NFC card whose password is known, it cannot be used for decrypting encrypted NFC card. For example, the default password of all blocks of Mifare Classic card is 0xFFFFFFFFFFFF. the Mifare card can be written/read only when the default password isn't changed
- This module can not be used to copy card, unless that the card use default password.
- This module can not be used to simulate NFC card. Because ID of NFC card are 4 bytes, because of security policy of PN532, it will set the first byte of simulate card to 0x08. For more details, please refer to http://www.nfc-tools.org/index.php?title=PN53x%E3%80%82
Applications
- Contactless payment system
- Bluetooth and WiFi devices chaining
- Social sharing function like sharing contacts, photos, and videos
- Smart phone NFC app
Specifications
- NFC Controller: PN532
- Operating Voltage: 3.3V/5V
- Operating Frequency: 13.56MHz
- Communication Interfaces: I2C, SPI, UART (default)
- Default Baudrate: 115200 bps
What's on Board
Testing by PC
You can quick test the module by connecting it to PC with USB to TTL module instead of Raspberry Pi
1. Hardware connection
| PN532 NFC HAT | USB to TTL Module |
|---|---|
| 3V3 | 3.3V |
| GND | GND |
| TX | RX |
| RX | TX |
2. Set L0 to L and L1 to L by jumpers 3. Connect USB to TTL Module to PC by USB cable 4. Open Serial assistant software, set it
| Key | Value |
|---|---|
| Baud rate | 115200 |
| Data bits | 8 |
| Stop bits | 1 |
| Parity | None |
| Flow control | None |
5. Check "HEX SEND" and "HEX SHOW"
6. Select correct serial port and open
7. Send data below to wake up FN532 module:
55 55 00 00 00 00 00 00 00 00 00 00 00 00 00 00 FF 03 FD D4 14 01 17 00
(Please refer to PN532 User Manual HSU wake up condition Chapter)
The response from PN532 module should be:
00 00 FF 00 FF 00 00 00 FF 02 FE D5 15 16 00
8. Send data below to scan Mifare Classic card(The blue card provided, hereafter called as "card")
00 00 FF 04 FC D4 4A 01 00 E1 00
Closing card to coil part of module, module scan it and response:
00 00 FF 0C F4 D5 4B 01 01 00 04 08 04 XXXXXXXXXX 00
XXXXXXXXXX in response data is ID (3 bytes) and checksum (1 byte) of card.(Please refer to PN532 User Manual InListPassiveTarget Chapter)